Imagine trusting your favorite grocery store for years. One day, someone sneaks in, tampers with everyday items, and places them back on the shelf. Customers buy them without realizing the danger. That’s what just happened in the JavaScript world—a major supply chain attack that shook the trust of millions of developers.
What Happened?
It all started with a tweet from Ledger’s CTO, Charles Guillemet. He reported that there had been an attack that threatened the security of our wallets.
The NPM account of a well-known developer was compromised after a phishing email tricked them into handing over their credentials. With that access, attackers pushed malicious updates to widely used packages like chalk, strip-ansi, and color-convert.
These aren’t niche tools. They’re the invisible “ingredients” baked into countless apps. Together, the affected packages had been downloaded over 1 billion times, which means the risk touched nearly every corner of the JavaScript ecosystem.
The Goal: Stealing Crypto

The injected code was designed to hijack cryptocurrency transactions. It acted like a crypto-clipper, secretly swapping wallet addresses so that funds would go to the attacker instead of the intended recipient.
To make it harder to notice, the replacement addresses were chosen to look almost identical to the real ones. This trick preyed on human inattention, hoping users wouldn’t catch the small differences.
The code even hooked into popular blockchain activity, targeting Ethereum, Solana, and other chains. For people using regular software wallets, this kind of attack could have been devastating.
Why the Attack Failed
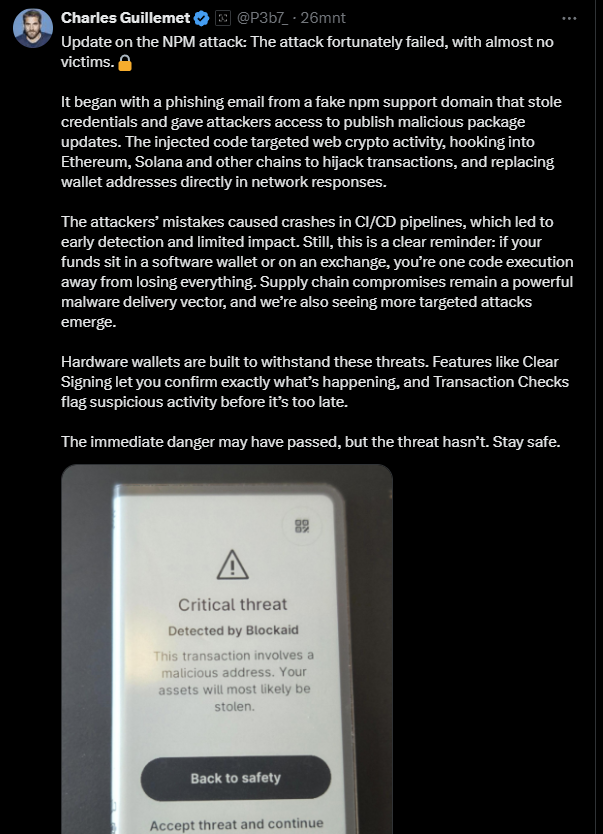
Here’s the fortunate twist: the attackers made mistakes. Their code caused automated build systems to crash, which raised early red flags. Developers quickly investigated, uncovered the malicious updates, and reported them.
Many wallet developers and other web3 project developers have posted on X stating that their systems are safe from hacking.
The impact was limited, and almost no victims lost funds. But this close call shows how fragile our digital supply chains can be. A single compromised account put billions of downloads at risk.
The Role of Hardware Wallets
One clear lesson stands out: how you store your crypto matters.
- Hardware wallets are built for scenarios like this. They let you verify every transaction with features like Clear Signing and flag suspicious activity before you approve anything. Even if your computer is compromised, a hardware wallet acts as your final safety net.
- Software wallets or exchange wallets, however, are more exposed. If malicious code sneaks in, your funds could vanish with just one careless click.
That’s why experts recommend pausing on-chain transactions if you don’t use a hardware wallet until threats like this are fully resolved.
How to Protect Yourself

Here are a few simple steps anyone can take:
- Double-check transactions – Always confirm wallet addresses carefully. Even one character off could mean your funds go elsewhere.
- Prefer hardware wallets – They add an extra layer of protection no software wallet can match.
- Keep your apps updated – Developers and security teams often patch issues quickly, but only if you install the updates.
- Watch for phishing – The root cause was a fake email. Always verify senders before clicking links or entering credentials.
So..
This NPM attack may not have succeeded, but it was a warning shot. Supply chain compromises are powerful, and next time the attackers may not make such obvious mistakes.
Think of it like a fire drill. The building didn’t burn down, but the alarms went off, and we got a glimpse of how unprepared we might be if disaster truly struck.
So whether you’re a developer, a crypto user, or just someone who relies on apps daily, remember this: stay alert, stay updated, and treat your digital safety like a priority.
You can follow me here on my website and my Medium to get my latest updates as soon as they drop! You can also contact me through X @AskaraJr and Linkedin



